CISPA, Saarland University, Saarland Informatics Campus
Abstract:
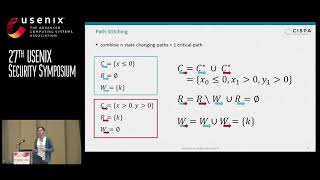
Cryptocurrencies like bitcoin not only provide a decentralized currency, but also provide a programmatic way to process transactions. Ethereum, the second largest cryptocurrency next to bitcoin, is the first to provide a Turing-complete language to specify transaction processing, thereby enabling so-called smart contracts. This provides an opportune setting for attackers, as security vulnerabilities are tightly intertwined with financial gain. In this paper, we consider the problem of automatic vulnerability identification and exploit generation for smart contracts. We develop a generic definition of vulnerable contracts and use this to build teEther, a tool that allows creating an exploit for a contract given only its binary bytecode. We p
View the full USENIX Security ’18 program at https://www.usenix.org/usenixsecurity18/technical-sessions


