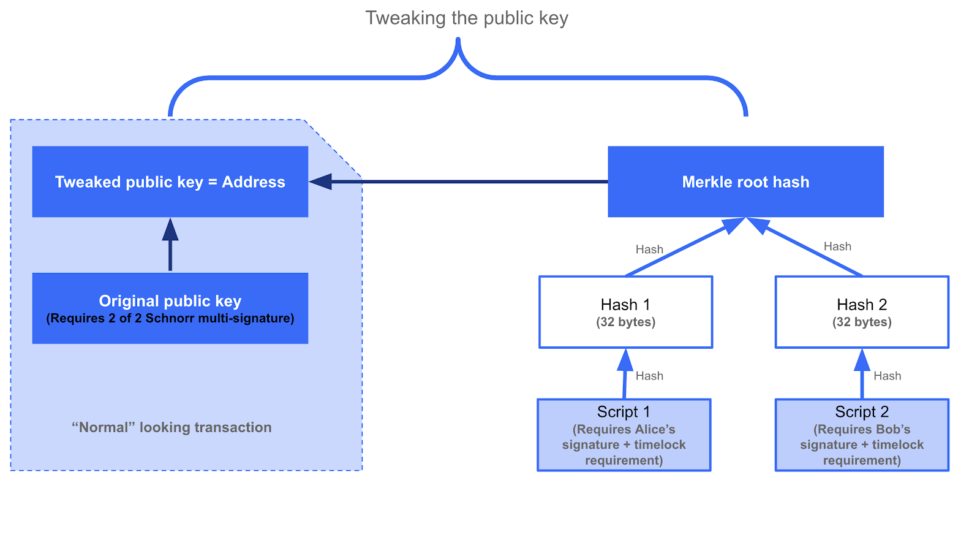
In the rapidly evolving world of digital currencies, security remains a paramount concern for users and investors alike. At the heart of bitcoin’s robust security framework lies the concept of public keys, a fundamental cryptographic element that enables secure transactions and wallet management. Understanding how public keys function is essential for anyone looking to navigate the bitcoin ecosystem safely. This article delves into the role of public keys in securing bitcoin wallets, explaining their nature, how they work in tandem with private keys, and why they are critical to maintaining the integrity and confidentiality of digital assets.
Understanding the Role of Public Keys in bitcoin Wallet Security
At the heart of bitcoin wallet security lies the use of public keys, cryptographic tools that enable transaction verification without exposing sensitive information. When you create a bitcoin wallet, it generates a pair; a public key and a private key. The public key functions as an address for receiving bitcoin, while the private key is a closely guarded secret that authorizes spending. This key pair ensures a robust layer of protection, allowing anyone to send funds to your wallet’s public key but only permitting the owner with the private key to unlock and transfer those funds.
Public keys are derived through a mathematical process that converts the private key into an irreversible format. This design is intentional because it prevents someone who sees the public key from calculating the private key. Such a one-way function is essential for the security and integrity of the bitcoin network, ensuring transactions are verifiable without revealing the user’s private credentials. The cryptographic link between these keys also guarantees that each transaction is digitally signed, confirming the ownership and preventing fraudulent use.
Key advantages of public keys in bitcoin wallets include:
- Enabling secure receipt of bitcoins without risking exposure of your private key.
- Allowing easy verification of transaction authenticity by nodes on the network.
- Providing users with unique, reusable wallet addresses that enhance privacy.
- Supporting multi-signature setups that increase wallet security.
To better understand their role, consider the simplified table below, showing the difference between key functions and visibility:
| Key Type | Function | Visibility | Security Role |
|---|---|---|---|
| Public Key | Receive bitcoin & verify transactions | Shared openly | Acts as wallet address; enables cryptographic verification |
| Private Key | Sign transactions & authorize spending | Kept secret | Confirms ownership and grants control over funds |
Cryptographic Principles Behind Public Key Generation
At the core of public key generation lies asymmetric cryptography, a revolutionary principle that uses two mathematically linked keys: one public, one private. The private key remains secret, while the public key is shared openly. This relationship ensures that data encrypted with the public key can only be decrypted by the matching private key, providing a robust foundation for secure bitcoin transactions.
The most commonly used cryptographic algorithm in bitcoin is the Elliptic Curve Digital Signature Algorithm (ECDSA). Elliptic curves provide a secure and efficient way to generate these key pairs by leveraging complex mathematical problems, such as the elliptic curve discrete logarithm problem, which is currently infeasible to solve with existing computing power. This complexity guarantees that a public key cannot practically be reverse-engineered to reveal its corresponding private key.
Key generation typically starts with a random number, known as the private key. This random seed is crucial because its unpredictability ensures wallet security.From this seed,the public key is computed via the elliptic curve point multiplication,a one-way function that produces the public key point on the curve. The safety of public/private key pairs relies heavily on:
- True randomness during private key creation
- One-way nature of elliptic curve multiplication
- Mathematical hardness of reversing key derivation
Below is a simplified comparison of cryptographic principles highlighting why elliptic curve cryptography is favored for public key generation in cryptocurrencies:
| Criterion | Elliptic Curve Cryptography (ECC) | RSA (Rivest-Shamir-Adleman) |
|---|---|---|
| Key Size | 256 bits (equivalent security) | 2048 bits or more |
| Computational Efficiency | High, faster key generation | Lower, slower calculations |
| Security Basis | Elliptic curve discrete logarithm problem | Integer factorization problem |
| Submission in bitcoin | Standard for wallet key pairs | Rarely used |
How Public Keys Enable Secure bitcoin Transactions
In bitcoin’s decentralized network, public keys serve as the essential cryptographic identifiers that enable the secure transfer of assets without exposing sensitive information. Each public key acts like a digital address, allowing users to receive bitcoins safely. When a transaction is initiated, the sender references the recipient’s public key to lock the bitcoins, ensuring that only the owner of the corresponding private key can unlock and spend them.
The security of these transactions fundamentally relies on the mathematical relationship between public and private keys. While the public key is shared openly on the blockchain, revealing the address where funds can be sent, the private key remains confidential, functioning as a cryptographic password that authorizes spending. This asymmetry is what makes bitcoin transactions both obvious and secure.
To better understand the interaction, consider the process of transaction validation:
- Address Generation: The public key is hashed to create a bitcoin address, an easily sharable form used for receiving coin transfers.
- Transaction Signing: The owner signs the transaction using their private key, which proves ownership without exposing the key itself.
- Verification: Network nodes use the public key to verify the signature’s authenticity before confirming the transaction.
here is a simple comparison of key roles within bitcoin transactions:
| Key Type | Purpose | Visibility |
|---|---|---|
| public Key | Receive bitcoins, verify signatures | Publicly visible on blockchain |
| Private Key | Authorize transactions, sign data | Strictly confidential |
Best Practices for Managing Public and Private Keys
Safeguarding private keys should be your highest priority when managing bitcoin wallets. These keys act as the ultimate proof of ownership and control over your funds. Store private keys offline in secure environments such as hardware wallets or encrypted USB drives.Avoid exposing them to internet-connected devices to minimize risks of hacking or malware attacks.
For public keys, while they are safe to share, it is wise to use different public keys for various transactions or addresses. This enhances privacy by preventing linkage of your entire wallet balance and activity to a single identity. Wallets with automatic key rotation features help in managing this complexity effortlessly.
Regularly backup your keys using multiple secure locations, preferably in geographically separate environments. Physical backups like paper wallets must be protected from environmental hazards such as moisture and fire. Digital backups should be encrypted and tested periodically to ensure recoverability, reinforcing continuity even if primary storage devices fail.
| Key Type | Recommended Storage | Primary risk |
|---|---|---|
| Private Key | Hardware wallet, Encrypted offline USB | Theft, Malware |
| Public Key | Wallet software, Shared openly | Privacy exposure (if reused) |
- Enable multi-factor authentication on any wallet services where possible for an extra security layer.
- Use passphrases along with seed phrases to protect against physical theft or brute force attacks.
- Keep firmware and wallet software up to date to benefit from the latest security patches and improvements.
Common Vulnerabilities and How to Protect Your bitcoin Wallet
bitcoin wallets, while designed with strong cryptographic principles, are not immune to vulnerabilities that can jeopardize your funds. One of the most common weaknesses arises from poor private key management.Losing your private key or exposing it to malicious actors means losing access to your bitcoins permanently. Always store your keys offline in hardware wallets or encrypted backups to minimize this risk.
another prevalent issue is phishing attacks. Attackers often impersonate wallet providers or send fraudulent emails to trick users into revealing their private keys or seed phrases. To protect yourself, never share your keys or enter them into suspicious websites. implementing two-factor authentication (2FA) on wallet platforms adds an essential extra layer of security.
Wallet software vulnerabilities can also expose users to risk. Outdated or unofficial wallet apps may contain bugs or backdoors that hackers exploit. Always download wallet software from trusted sources and keep it updated. For developers and advanced users, reviewing open-source wallet code or using community-verified versions further reduces potential threats.
Below is a brief overview of common vulnerabilities and recommended protection measures, summarized for speedy reference:
| Vulnerability | Risk | Protection Strategy |
|---|---|---|
| Poor Key Storage | Loss of access | Use hardware wallets, encrypted backups |
| Phishing Attacks | Private key theft | Verify URLs, enable 2FA |
| Outdated Software | Software exploits | Regularly update wallets |
| Malware | Keylogging and theft | Use trusted devices, antivirus |
Q&A
Q&A: Understanding Public Keys: How They Secure bitcoin Wallets
Q1: What is a public key in the context of bitcoin?
A public key is a cryptographic code derived from a private key that allows others to send bitcoins to a specific wallet. It acts like an address visible on the blockchain where funds can be received.
Q2: How is a public key generated?
A public key is generated through a mathematical process called elliptic curve cryptography (ECC) from the private key. While the private key must remain secret, the public key can be freely shared without compromising security.
Q3: What role does the public key play in securing a bitcoin wallet?
The public key enables customers to receive bitcoin without exposing their private key. It acts as a secure identifier that others can use to verify transactions and send funds, ensuring secure and transparent operations.
Q4: Can a public key be used to access or spend bitcoins in the wallet?
No, the public key alone cannot be used to spend bitcoins. Only the private key associated with the public key can authorize spending, thus safeguarding the wallet from unauthorized access.Q5: What is the relationship between public keys and bitcoin addresses?
bitcoin addresses are shortened and hashed versions of public keys, designed to make them easier to share and use. They are what users typically exchange when sending or receiving bitcoins.
Q6: Why is it safe to share your public key or bitcoin address?
Sharing your public key or bitcoin address is safe as they do not reveal the private key. They only allow others to send bitcoins to your wallet but not to spend or move your funds.Q7: How does the use of public and private keys enhance the security of bitcoin transactions?
This asymmetric cryptography system ensures that only the holder of the private key can authorize transactions, while the public key is used by others to verify the signature. This prevents fraud and unauthorized access.
Q8: What happens if someone gets access to your public key?
Access to the public key alone does not compromise your wallet security. However, it is good practice to maintain privacy to avoid potential targeting or phishing attempts.
Q9: Can public keys be reused for multiple transactions?
Yes, but it is generally recommended to use new public keys for each transaction to enhance privacy and reduce the risk of being tracked on the blockchain.Q10: How does the public key fit into the overall structure of bitcoin security?
The public key is a crucial part of the public-private key pair that underpins bitcoin’s decentralized security. It allows for secure receiving addresses and transaction verification, enabling trustless peer-to-peer digital currency transfers.
Insights and Conclusions
public keys play a fundamental role in securing bitcoin wallets by enabling safe and transparent transactions on the blockchain. By understanding how public keys function alongside private keys, users can better appreciate the cryptographic principles that protect their digital assets. This knowledge is essential not only for maintaining personal wallet security but also for fostering trust in the broader cryptocurrency ecosystem.As digital currencies continue to evolve, grasping the basics of public key cryptography remains a crucial step toward responsible and informed participation in the world of bitcoin.