Sentinel Protocol — Are your crypto assets safe?
Sentinel Protocol — Are your crypto assets safe?
Sentinel Protocol , by the Uppsala Foundation, is a blockchain-based cybersecurity startup that empowers security experts and crypto services around the world with timely threat data supported by AI, for a united and solid defense against hacks, scams and frauds.
Overview
Sentinel Protocol can be seen as ‘The Guardian of your Digital Assets’ , bringing ultimate security to the crypto universe through its integrated security intelligence solutions for the blockchain. Sentinel Protocol will be launched on the blockchain.

The rapid development of computer technology in the 21st century has led to the manifestation of sophisticated and intelligent threats that hinder further innovation. While the essence of cryptocurrency is decentralization, this has also become its greatest weakness. As the decentralized cryptocurrency system lacks a threat defense system, the burden for security has thus far been placed squarely upon the shoulders of individuals and corporations.
Sentinel Protocol overcomes the disadvantage of decentralization by turning it into an advantage for security. By utilizing a collective intelligence system created through harnessing the power of decentralization, Sentinel Protocol combines cryptographic functions and intelligence-based threat analysis algorithms to create a secure, innovative ecosystem.
Product, Technology and The Use of Blockchain
Sentinel Protocol can be described as security intelligence platform for blockchain (SIPB), this includes a wide variety of security features, from anti theft, malformed transaction prevention, unknown threat prevention, transaction traceability etc.
The protocol collects hacking reports, which are then delegated to “The Sentinels”, a group of trusted security experts, who confirms the incident and registers the case information to the Threat Reputation Databse (TRDB).
The Sentinels are rewarded for participation under the model with Sentinel Points (SP), which can later be redeemed for its native currency UPP.
Sentinel Protocol also introduces their own S-wallet, a secure wallet with built in machine learning AI, Fraud Detection System (FDS) and built-in security features such as filtering scam addresses and detecting abnormal behavior, leveraging TRDB for always up-to-date threat definitions. Sentinel Protocol utilizes the strength of decentralized and distributed computing, running extensive tests and simulations in their D-Sandbox (Distributed Malware Sandboxing) environment, effectively cutting cost down compared to the traditional expensive dedicated virtual machine environments. Sentinel Protocol can be integrated seamlessly to any client wallets and exchanges, leveraging its collective intelligence to protect users from malicious threats.
Key Security FeaturesThreat Reputation Database (TRDB)
Those who have used anti-virus softwares for the internet should be familiar with definition files, each commercial virus scanners maintain their own virus/threat database and end-users need to update on a periodic basis for the latest definition. These databases are not only centralized making them more vulnerable to manipulate but more importantly never complete as vendors lack any incentive to collaborate. Sentinel Protocol aims to create a global alliance for threat information exchange, with built-in incentives for each vendor to contribute to the TRDB.
Machine Learning Engine Integrated Security Wallet (S-Wallet)
Sentinel Protocol’s secure wallet (S-wallet) is similar to an “antivirus enabled wallet”, leveraging collective intelligence harvested by the community and security experts pooled in the TRDB. S-wallets can detect suspicious executions, these can be in the form of blacklisted wallet addresses, scam sites or fradulent activities detected by their Fraud Detection System(FDS), driven by their proprietary machine learning engine. S-wallet also analyzes the threat tendency and history to proactively respond to unknown threats (known as zero-day attacks) that traditional antivirus softwares can’t do before the next software update. This is an AI driven engine, continuously learning from the client side Sentinel Wallet to create model behaviors.
Let’s create a use case to see how this might work in real life. Say you’re about to participate in an ICO, and ICOs these days come with scams by default. There’s a telegram DM popped up on your phone, with a contribution address that will expire in 3 min, it’s been a busy day that you’re not keeping up with the latest update and you are about to FOMO in.
Now when you enter the contribution address into your S-wallet, ready to send the transaction, the send button suddenly turns red with (13 SCAMS REPORTED), you know S-wallet just saved your hard earned(?) ETH.
Distributed Malware Analysis Sandbox (D-Sandbox)
D-Sandbox is similar to traditional sandbox, a test environment (virtual machines) to run unverified programs. In D-Sandbox environment (decentralized nodes), potential threats are submitted and analyzed thoroughly via collective intelligence, at significantly lower costs of computing resources and infinitely scalable.
For blockchain part we are intended to using ICON as platform for the time being you can refer ICON’s GitHub.Token Utility
There are 2 different digital tokens existing in the Sentinel Protocol ecosystem:-
The first is the platform reputation point called Sentinel Point (SP). An important concept dictating how these SPs are awarded and who are eligible to earn them is the consensus mechanism concept of Delegated Proof of Stake (DPoS).
Delegated Proof of Stake
DPoS is a system in which only qualified entities/nodes are specially delegated/selected to be representatives for consensus on the blockchain.
In the case of Sentinel Protocol, only individuals or institutions with cybersecurity expertise will be specially delegated by the Uppsala Foundation to carry the coveted title of Sentinel, acting as elite members tasked with protecting the rest of the crypto community. In most cases, only Sentinels will be able to earn SPs.
White hat hackers and cybersecurity experts who have answered the call to become Sentinels, provide meaningful contribution to the safety of digital assets — such as submitting security data, advice, research and analysis to help prevent hacks and scams. Each action is known as a Proof of Protection (PoP) . As a reward for their efforts, they receive Sentinel Points (SPs).
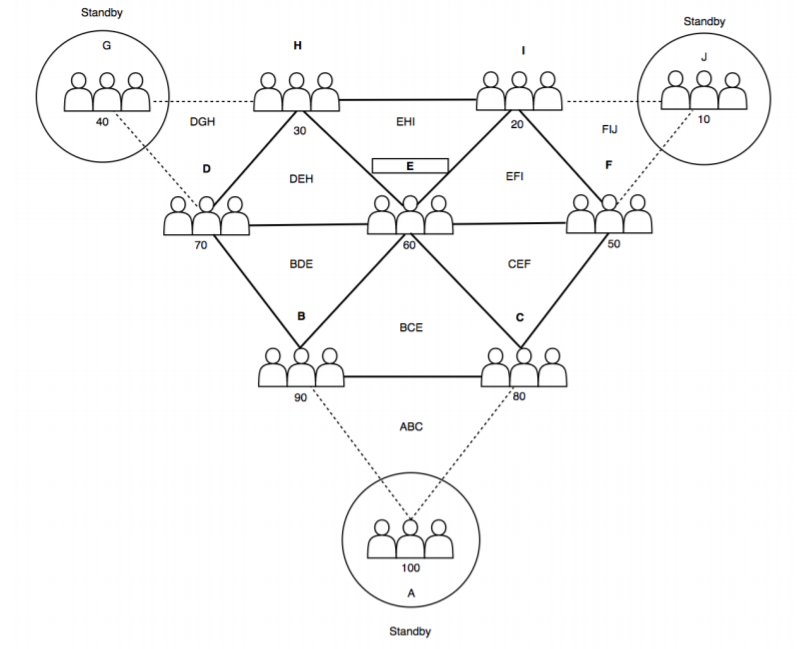
As part of the peer review-based Proof of Protection (PoP) reputation system, Sentinels are assigned into special groups of 7, with 3 Sentinels on standby. These 7 Sentinels in each group run routine tasks eg. validate transactions, generate blocks and update the threat database, and render higher level assistance when necessary. The 3 reserve Sentinels on standby help prevent DDoS (Distributed Denial of Service) attacks — multiple spam attacks on a program or website that cause it to exceed its bandwidth and stops normal operations for users.
Sentinel contribution/Proof of Protection examples include, but are not limited to:
Helping victims recover funds lost to hacksValidating hacking claimsIdentifying root cause of threatsConducting research and analysisBoosting the security intelligence of the Decentralized Threat and Reputation Database (TRDB) through regular updatesContributing to the wider crypto community i.e writing articles on cybersecurity
*The 3 human figures in the diagram represent 1 Sentinel entity (which could be an individual or an institution).
The Sentinels’ reputation is always at stake. If they fail to carry out their duties properly, they get a poor reputation score, and run the risk of being disqualified as a Sentinel. Those that excel in their duties gain a better reputation score and earn more SPs.
As such, Delegated Proof of Stake (DPoS) and Proof of Protection (PoP) together form an efficient consensus mechanism and incentivized reputation system which keeps the Sentinels in check and motivates them to enhance their cybersecurity efforts.
Sentinel Points (SPs) are not for sale, only earned through PoP.
SPs are valuable because they can be converted into UPP tokens. UPP tokens can in turn be bought and sold on the open market i.e crypto exchanges.
SP holders are also entitled to receive UPP tokens generated through an automated vesting schedule. According to the whitepaper, vesting amount will be proportional to the SPs each entity holds, relative to the total SPs generated via Proof of Protection (PoP) done in a certain period of time. This UPP token generation model is designed to reward early contributors to the Sentinel Protocol.
UPP tokens are ERC-20 tokens based on Ethereum. Once ICON’s mainnet has stabilized, UPP tokens will be converted into ICON-based tokens through a special process. ICON has been selected due to higher (expected) speed and scalability compared to Ethereum, as well as the promise of cross-chain interoperability.
The Sentinel Portal, TRDB, API Integration and other basic services will be provided to the public for FREE. But it is mandatory for UPP digital tokens to be used as a cryptocurrency payment to access Sentinel Protocol’s more advanced and premium features:
Machine learning-based anomaly detectionDistributed malware SandboxingThreat case submissionsHow will UPP grow in value?
UPP tokens are utility tokens needed as currency within the Sentinel Protocol platform. Greater adoption of the platform will naturally increase the purchase and the value of the tokens.
Who are willing to purchase more UPP tokens so that they can use Sentinel Protocol’s advanced features such as machine learning-based anomaly detection or distributed sandboxing?
Individuals or companies that have a lot of digital assets under management and are motivated to pay good money to procure the highest level of security to protect their funds. Examples include: Crypto exchanges, crypto wallets, ICOs accepting money and payment services.
These advanced features will be more effective when more cybersecurity experts and agencies are incentivized to participate in the Sentinel Protocol platform. When the security solutions provided on the platform are more robust, there will be a natural increase in crypto businesses and individuals coming on board to use its API integration to beef up their cybersecurity.
Team“Founders should have a history before they start a company — otherwise, they are just rolling the dice.”– Peter Thiel
The Uppsala Foundation is the company and team behind Sentinel Protocol and the namesake of their UPP token.
Cast into the spotlight after their in Korea, and being finalists in the , the team is revealed to be a hardworking, respectable outfit that goes the extra mile to participate in blockchain competitions to prove their worth.
The team has vast cybersecurity experience, and some of them have worked together for over 5 years.
CEO Patrick Kim himself had worked in Cisco, Paolo Alto Networks, F5 Networks and Darktrace — all well-known enterprise security companies. Many team members also share similar professional experiences. For instance, Head of Operations HM Park and Chief Evangelist John Kirch both also worked at Darktrace before.
The connection is interesting due to the company’s use of machine learning in cybersecurity, and we are sure the Sentinel Protocol team will bring over some of its best practices to their own AI solutions.
Head of Marketing Karly Choi has prior experience in cybersecurity companies, having worked for Cloudbric. She is a regular presence on Telegram and roadshows, faithfully answering the community’s questions.
The name Uppsala is named after an old capital of Sweden, where the founder Patrick Kim and co-founder HM Park stayed and conducted some study over blockchain focusing on lightning consensus algorithm, the idea of Sentinel Protocol was also drafted there.
Over time, Uppsala Foundation will evolve into a truly decentralized organization. In the beginning, Uppsala Foundation is needed to initiate the platform and review the applications for the role of the “Sentinels”. Through a vigorous vetting process, we will select the best applicants to fulfill the role. However, when the platform becomes self-sustainable and self-governed, the
Sentinels will be chosen by the community itself. Uppsala Foundation (UPP) tokens will be circulated to pay for advanced security features like S-Wallet and D-Sandboxing. Uppsala Foundation members will shift focus toward providing the community with new and innovative products beyond S-Wallet and D-Sandboxing
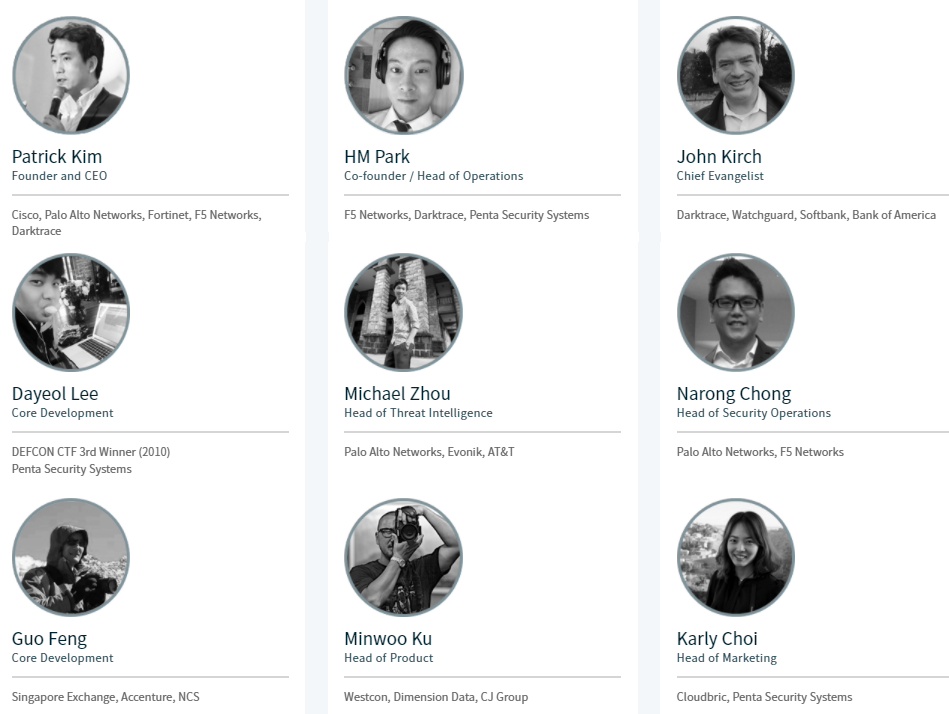
Patrick Kim (Founder and CEO) |
HM Park (Co-founder / Head of Operations) |
John Kirch (Chief Evangelist) |
Dayeol Lee (Senior Researcher and Engineer) |
Michael Zhou (Head of Threat Intelligence) |
Narong Chong (Head of Security Operations) |
Guo Feng (Core Development) |
Minwoo Ku (Head of Product) |
Karly Choi (Head of Marketing) |
Advisors
You can’t do everything on your own and sometime you need the ones who will help you to take and then maintain the right path. The best advisors help in three ways: encourage you to look at the problem or opportunity from multiple angles; help you balance the tug of the short-term with important long-term priorities; and ask the tough questions you need to know to reach the best solution.
Sentinel Protocol has a solid board of advisors. Here are the ones who’s going to help the Sentinel team realize their goals:

Simon Kim is CEO and Partner of Hashed, a leading crypto fund based in South Korea. He is a Blockchain evangelist and organizer of Hashed Lounge, a premier Blockchain Seoul meetup community.
2. John NgPartner at Signum Capital
John Ng is the founder of Signum Capital, an investment vehicle specialized in ICOs.
3. JH KimFoundation Council at ICON
JH Kim majored in computer science and engineering at POSTECH University, and has worked in the field of information security for nearly 20 years.

HongZhuang Lim is a serial entrepreneur and the Chief Executive Officer at XSQ Blockchain Infrastructure and Investments Company.
5. Wong Lee HongExecutive Advisor at Kyber Network
Wong Lee Hong is a Blockchain growth investor at present, but his career spans across various industries over 3 decades. He has extensive distribution and business development experiences in consumer electronics, multimedia, computer gaming, Internet, and the banking sectors.
6. Kenneth OhSenior Partner at Dentons Rodyk & Davidson
Kenneth Oh is a practising lawyer and Senior Partner with Dentons Rodyk & Davidson’s Distributed Ledger & Blockchain Practice, Corporate Practice as well as China/Indonesia Practices.
Current and potential partners
#HASHED has invested in some of the top ICOs in the world, including , , and . We believe that as one of the key projects being accelerated by the top Korean crypto investment fund, Sentinel Protocol has definitely passed the due diligence of blockchain, cybersecurity and investment experts.

#HASHED is also in the esteemed company of other well-known funds and , and blockchain project partners such as top korean crypto wallet . Overall, Sentinel Protocol has a pretty solid lineup of investors and partners.

The growth of crime in the field of computer security has obliged company owners to invest more and more to protect business.
A study shows that the first major cybercrime incident on Ethereum was in June 2016. A mistake in a DAO intellectual contract led to $74m of an invested $150m being stolen by an attacker.
One of the most popular forms of contract for Ethereum are tokens. More than 800 tokens have been released on the Ethereum platform since its launch in 2015.
In 2017, $1.6bln was invested in ICOs based on Ethereum, but cybercriminals were able to steal more than $150m of income. About 10% of tokens passed through ICOs were in the hands of criminals.
The growth of cybercrime on Ethereum grew in tandem with ICO funding increases, while the total damage from cybercrime grew from $100m in June to $225m in August this year.
In 2024, the world market for ICOs will be worth $20 bln. This figure is stated in a report from the American analytical company Transparency Market Research. The industry will grow by an average of 59% per year. The research is constituted on the blockchain market of 2015, whose volume was estimated at $316 mln.
More and more companies are showing interest in blockchain technology, but basic software does not meet key requirements such as efficiency, confidentiality, management and required computing power. All these factors attract more and more hackers to the technology.
All this entails the need of potential investors to protect against hacker attacks. According to the forecasts of IDC’s analysts, the world sales for hardware, software and services related to computer security will grow by 8.2% to $81.7 bln in 2017. In the coming years, growth will accelerate — an average of 8.7% per year — and by 2020 the market will grow to almost $105 bln.
Digital transformation forces companies to invest actively in security equipment. More than 30% of purchases come from companies in banking, discrete and government sectors. Faster than in other sectors (11.2% per year) the telecommunications industry is stepping up its purchases, and it will enter the top five largest buyers in 2018.
The largest segment of the market in the coming years will be services — primarily managed security services, as well as integration and consulting services. These account for almost $31.2 bln in 2017. The size of the segment for hardware and software network security will be $15.2 bln in 2017, and endpoint security tools will be $10.2 bln. Other actively developing spheres are software (16% per year) and program (14.5% per year) vulnerability assessment segments, managed security services (12.2% per year), user behavior analysis (12.2% per year) and unified threat management (UTM) (11.9% per year).
CompetitionAs told by the Sentinel Team: It’s great to see new projects tackling blockchain cybersecurity and to witness this vital field expanding. Just a year ago, we did not see anything like this. It is hard to tell what competitive advantages a project has over another because almost all projects are still in the early stages with no working products or security features available on the market.
However, in terms of value proposition and grand vision, we are unaware of any companies doing exactly what we are doing. Note how we positioned ourselves as a ‘protocol’. One of our key goals is to become the standard protocol for the blockchain security industry. Both traditional and crypto cybersecurity companies are not our competitors. We consider them as potential Sentinels and they are welcomed to join our ecosystem. We are opening up an opportunity for traditional cybersecurity companies to add blockchain security to their experience. Cryptosecurity companies focused on providing transaction data, data analytics, or Know Your Customer (KYC) validations are also our potential partners. Cybersecurity vendors and individuals are economically incentivized to share data and contribute to the Sentinel Protocol’s ecosystem.
But we think there are some indirect competitors in both Blockchain and Non-Blockchain space including , , , etc.
Since, Sentinel is taking a novel approach to the cyber security using the Blockchain technology, we think it’ll be way above the quality and efficiency in the cyber-security world, once deployed for the public use in the future.
Media Coverage and CommunityHype Rate: Medium growing to HighSimon Kim, CEO of the famous Korean crypto investment fund :
“Sentinel is an essential blockchain project as it can cultivate trust even outside the blockchain environment where hacking and fraud are rampant.”
The team has been making an effort to spread awareness, with lined up, even attending most of them with the popular ICON foundation team.
They have also been very friendly and responsive on Telegram, encouraging everyone, especially those with cybersecurity knowledge, to participate in the program.
Most of the hype is due to their association with the and projects.
At the time of writing, Sentinel Protocol has over 7500 supporters on . Followers at 1704 with Number of Tweets equals 52 till date considering Twitter Joining Date be Jan,2018. Page Followers rests at 211 and Reddit Subscribers at 41 (They need to work on their social media strategy, also considering Reddit is now a primary location for crypto enthusiasts to discuss about different projects). The Alexa Rank (GLOBAL RANK) rests at 700734 which is rather low considering this project is launching in few weeks.
Although it is clear that Sentinel Protocol has raised the bulk of the money they need through their private sale, it is important to eventually ramp up engagement not only with their exclusive club of accredited investors and cybersecurity firms, but also with the general crypto community as well.
For easier dissemination of information and to aid visual learners, there is a desperate need for a Youtube introductory video on their website.
Subsequently, an infographic contest can be held as well to turn the complex mechanics of the Sentinel Protocol project into a simple, easily digestible visual illustration.
Some kinds of enticing referral and bounty system should also be deployed. Referrals are one of the most popular and successful ways ICO companies spread awareness about their projects and so far it has given amazing results.
Lastly, the concept of ‘The Sentinel’ — a soldier that stands guard and watches for enemy threats — is a very powerful symbol that should be used prominently in their marketing. A good graphic designer should be hired to produce an eye-catching Sentinel icon (separate from the official project logo) for maximum impact. Currently, the Sentinel Protocol logo is cool, but doesn’t remind someone of an actual ‘Sentinel’ watchdog.
Cybersecurity experts are needed to be Sentinels, while general crypto investors could be Sentinel Protocol evangelists — sharing about Sentinel Protocol’s services and how to prevent cyber threats. Without some level of hype, this project runs the risk of remaining inside a very niche, technical field, within an already tiny subculture of cryptocurrency enthusiasts.
Jargons and Buzzwords — (3/5)
We have a small gripe on their use of acronyms, in particular ‘TRDB’. The Decentralized Threat Reputation Database is already a mouthful to begin with. Providing an acronym is great, but in this case it ends up being confusing, as going by the leading alphabets, it should be a lot easier for the masses to understand.
There are already many other acronyms to remember, such as SIPB (Security Intelligence Platform on Blockchain), DPoS (Delegated Proof of Stake), LFT(Loop Fault Tolerance) and FDS (Fraud Detection System).
We don’t think the point here is to scare away hackers away with complex nomenclature.
We believe in simple nomenclature which are much easier to remember and still explain literally what the service is about.
Similarly, we find the naming of the UPP currency token rather strange. Uppsala is a city in Sweden, and also the place where the Sentinel Protocol idea originated — hence the inspiration behind the company’s name. But it has absolutely nothing to do with the tech or the token architecture and only serves to further confuse participants. Ideally, there should be a clear distinction between Uppsala the security company and Sentinel Protocol the actual product/service.
It is understandable that the label ‘Sentinel Point’ is already used for the reputation score layer, and in order to prevent confusion, another name is required for the digital currency token to be used for advanced features on the platform.
Whitepaper includes most of the technical topics and details which shouldn’t be very hard for a person to understand. So, points for that. However, we take issue with the roadmap, which is slightly less detailed and only includes milestones. More details are always appreciated.
Token Sale Information
PreSale and ICO Limits (Max. cap in ETH) — 0.5–10 (30–300 for Presale)
Pre-Sale Start Date — 7-May-2018
ICO Start Date — 11-May-2018
Presale Price ( in USD ) — 0.0697
ICO Price ( in USD ) — 0.082
Total Tokens — 500,000,000
Maximum Fund Raised before ICO in USD — $11,000,000
Token Sale Hardcap ( in USD) — $11,670,000
Percentage of token distribution in ICO ( in % ) — 60.00%
Token Market Valuation at ICO — $24,600,000
Token Lockups — Yes (Bonus — 15%)
Maximum Discounts ( in % ) — 15.00%
Token type — Utility
Left tokens burnt — Yes
ICO TYPE — Airdrop + Normal
Exchange listing announced — No
Crypto VC Fund Participating — Yes
Token Distribution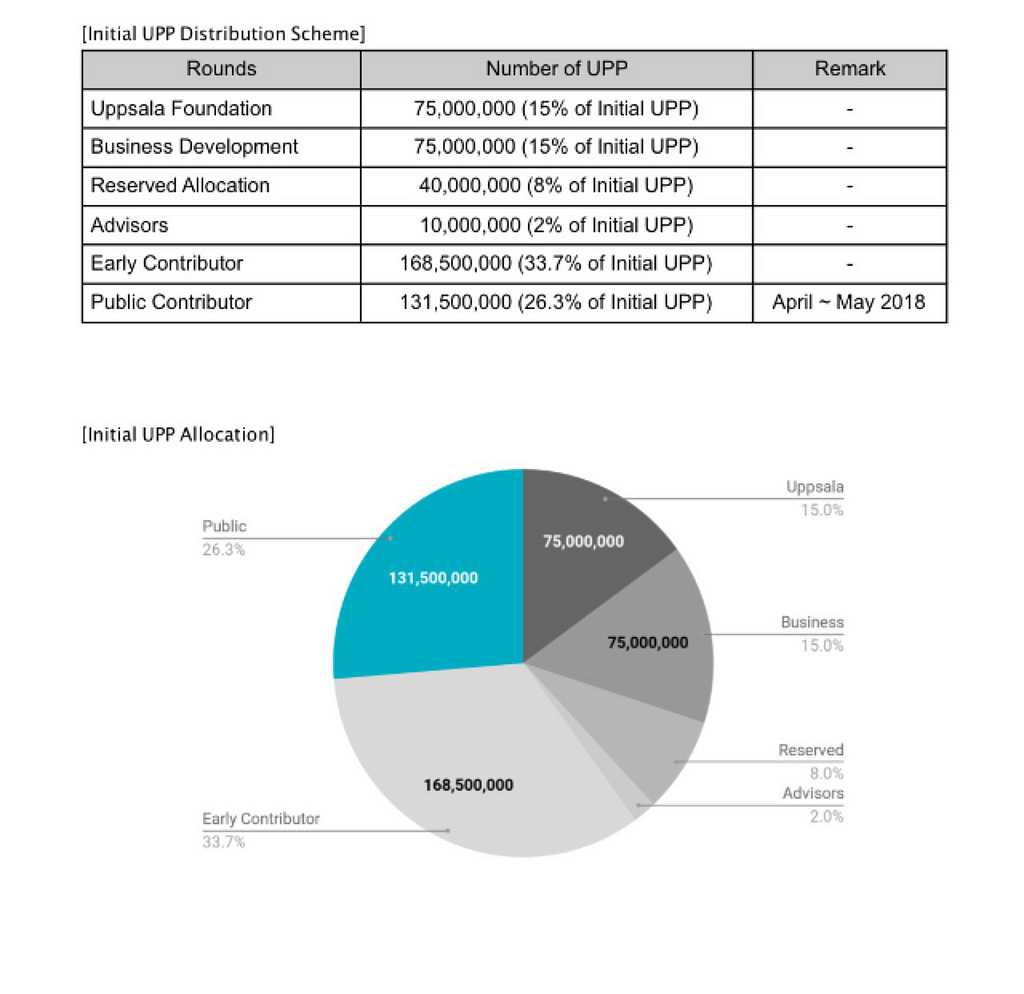
Of the total 100% supply, 60% is intended for the public and 40% reserved. Of the 60%, 56.17% went to private contributors, 43.83% went to public sale. Of the public sale, 3.8% were for pre-sentinels free airdrop, 66.5% will go to presale and 28.75% go to crowdsale. 66.5% was further broken down to public presale and strategic contributors, 50% each.
Vesting period is 2 years (24 months) for Team and Advisor Tokens.Usage of Funds

100% compliant to SEC and other international regulations.
Registered in Singapore and you can find address and registration number in below link.
They are working with Cynopsis for KYC verifications. you can refer the following link about them they are well proven 3rd party KYC company.
Conclusion
Security is the fundamental layer of any meaningful projects, exchanges and DAPPs. The crypto universe is to a great degree dangerous place. With inadequately coded sites and dApps, and man-in-the-middle scams will always be there in any nascent technology and it will keep on, as the technology evolves.
With a team of great individuals consistantly working towards the security of our digital assets it is especially comforting to know that the world’s top cybersecurity experts are being constantly incentivised to protect our digital assets.
We strongly believe Sentinel Protocol is largely very effective, and will play a crucial role in protecting the crypto community’s digital assets. We hope that every centralized or decentralized exchange out there will become part of the Sentinel Protocol ecosystem.
Based on our Cointify Sharks ICO Framework, Sentinel Protocol is a respectable project and receives a Good score of 69.32%. We are looking forward for MVP — live public testing on the website, a more detailed roadmap, greater community engagements, and an egalitarian token distribution. Still, we’re very bullish on this project and looking forward for further development updates from the Sentinel Team.
Sentinel Protocol Contact InfoWebsite:
Disclaimer: This post is for educational and informational purposes only and not to be considered as an investment advice. We’re neither endorsing nor promoting any of the projects mentioned in this post. You should consult with a financial advisor or other professional to determine what may be best for your individual needs and risk tolerance. Always do your own research.
Reach out to Cointify Research Network for Blockchain Research, ICO and Token Analysis, Investment and Education on
was originally published in on Medium, where people are continuing the conversation by highlighting and responding to this story.
ecosystem overview
Problem Issues
Monitoring of multi-billion market of industrial products group and rapidly growing e-commerce market has revealed the lack of bridge between an end- customer and a manufacturer, that will enable direct communication between them, promoting loyalty and client- oriented approach.
Yodse’s main purposes.
The platform yodse aims to become the largest Internet ecosystem for the most convenient, rapid and profitable interaction of enterprises in the field of production of industrial product groups in the markets of Russia, CIS, South-East Asia, and later in Europe and the United States. This global, decentralized and transparent B2B / B2C trading platform has all the advantages of blockchain technology and thus provides manufacturers with the most convenient communication with their wholesalers and retail buyers. The scale, high-tech products and convenient user-friendly tools within the ecosystem will allow small and medium-sized businesses to achieve better results and gain practical benefit.
Challenges that yodse ecosystem solves
yodse project is aimed at solving a number of problems related to direct, convenient, rapid and profitable “manufacturer-consumer” interaction. The transparent ecosystem yodse focuses on the protection consumers from losses, connected with the lack of guarantees from manufacturers and abundance of poor-quality goods. By establishing communication mechanisms, buyers will be provided with technical support, and manufacturers will receive quality feedback. The platform will reduce the delivery time and enable consumers to purchase goods without intermediaries. Excessive costs of manufacturers for outdated marketing technologies and high fees of goods placement on existing e-commerce platforms will become history. The YODSE system offers its users low fees and creates conditions for easy access of small businesses to e-commerce and international markets.
Advantages of using ecosystem (platform) yodse for manufacturers
The yodse electronic platform and its tools allow businesses, operating in the production of industrial product groups to find their retail and wholesale customers and to provide direct sales without intermediaries. The system helps to set up a mechanism for communication with clients, enhance the transparency of transactions, perform transparent management and control in the process of delivery and payments, and expand the customer base, maximize the volume of goods turnover and net profit. In addition, owing to the global system based on the blockchain technology, small and medium-sized businesses will be able to solve the problems of entering new promising markets, as well as significantly improve the competitiveness of manufactured industrial products.
Advantages of using ecosystem (platform) yodse for consumers
Yodse project gives huge advantages for users while searching and purchasing industrial products group, motor vehicles, production, road construction, mining and agricultural machinery, material handling equipment, rigging arrangement, turbines, equipment for ventilation and air conditioning, pumps, compressors, bearings and others. Direct prices from manufacturer without intermediaries allow to maximize profit and users feedbacks and quality technical support from manufacturers will enable consumers to learn more about the product and make sure of its quality.
Use of crypto-currencies and traditional forms of payment within the system.
Using the platform, consumer can choose from a wide range of necessary industrial products from domestic or foreign manufacturers, for which it will be possible to pay with BTC / ETH / XPR crypto-currencies, yodse tokens as well as national currencies. As the number of users of the platform increase, the number of transactions made in crypto-currencies will increase significantly, however in the countries where the turnover of crypto-currency fall under the restrictive regulation, traditional currencies will be used. With regard to the use of yodse tokens, these elements of the ecosystem, based on the cryptographic algorithm based on Blockchain technology, will help increase user loyalty and give owners the opportunity to perform transparent and conflict-free operations, confirmed by smart contracts, pay for platform services, make token loans, become a member of the referral program and receive revenue from sales. In this case, yodse tokens are not securities, however as the number of users and transactions on the platform grow, the tokens value will increase as well.
Why this particular direct sales platform will be the most promising and highly- demanded
yodse global platform is a unique platform and has a number of advantages that distinguish it from other platforms. The most important advantage of this platform is transparency of transactions owing to blockchain technology and possibility to conduct transactions with crypto currencies. In addition, users will receive quality In continuous 24/7 support, available product localization, a transparent feedback system, prices from manufacturers, so that they will be able to derive maximum benefit from the purchase of quality products.
YODSE ecosystem growth prospects
Benefits for users from yodse ecosystem scaling.
Joining of a number of manufacturers of industrial groups of goods to the yodse system will make it possible to conclude a lot of mutually beneficial, multimillion contracts. As the yodse platform dynamically develops and scales, there will be a gradual increase in the number of offices being opened in many regions in order to provide quality and continuous technical support to users in other countries and maintain the brand. The scaling of ecosystem will enhance the frequency of use of the platform in a number of countries, which will increase the number of users, thereby facilitating the establishment of export-import transactions between countries and, as a result, increase sales volumes of manufacturers. Manufacturers, who sign in earlier than others, will take the advantages of being pioneers in new markets.
Which countries, markets, continents will cover YODSE ecosystem?
The expansion of the yodse ecosystem geography is planned to begin in the markets of Eastern Europe and the countries of the Customs Union (Russia, Kazakhstan, Belarus, etc.), which are leaders in the production and procurement of industrial groups of goods. In the future, creators of the platform plan to expand the ecosystem and enter overseas markets, expanding the scope of their activities to the countries of the Asian region, Africa, Latin America. In the mid-term perspective yodse platform plans to cover the market of Europe, USA and Australia.