and are partners at Primitive Ventures, a crypto asset investment fund.
–––––––––
Recently, there has been discussion regarding a proposal to migrate away from proof-of-work called (). Proponents of ProgPoW want to flip the paradigm of the industry on its head. Their thought is: instead of building hardware to fit the algorithms, a somewhat “wasteful” approach, we should be using algorithms that are optimized for GPUs to encourage the decentralization of .
At first glance, ProgPoW appears to minimize the advantage ASICs have over commodity hardware, making more accessible and thus decentralized. But upon further inspection, it becomes evident that ProgPoW doesn’t truly democratize as it claims.
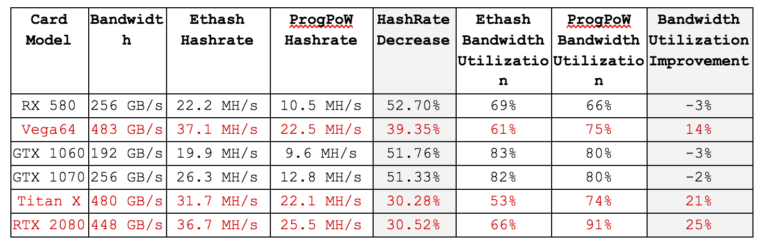
The current implementation of ProgPoW, in fact, worsens the performance gap between the different GPU models, with preference given to the newer and more expensive GPU models from NVIDIA and AMD (the RTX 2080, TitanX and Vega 64). The team behind the proposition has been transparent about the fact that the algorithm is optimized for certain GPUs, and they are actively working on a newer version of the algorithm to make it more fair to all models.
(We will update the performance benchmark here once it’s available.)
The table below illustrates the hashrate reduction comparison between ’s current algorithm, Ethash, and ProgPoW for different GPUs. Highlighted in red are the models ProgPoW favors, which see a much smaller decrease in hashrate and greater improvement in bandwidth utilization under ProgPoW.
The implementation of ProgPoW in will potentially serve to centralize further in the hands of those farms which have these high-end GPUs, or urge farm owners to upgrade to those models.
Source:
A nonexistent problem
Putting that fact aside, the “ASIC threat” that ProgPoW purports to solve is actually not as much a problem as one might think. Even ProgPoW developers acknowledge that ’s algorithm is already one of the most ASIC-resistant. The best ASICs have a tough time achieving a mere 2-4x improvement over GPU , far less than ASICs.
Vitalik Buterin, the founder of , is also not concerned about the threat ASICs pose, : “If you look at the E3 that was released a few days ago the efficiency gains are relatively small compared to existing GPUs. My Chinese sources indicate a 220 MH/s miner costs about $2,500, while Bitmain is offering a 180 MH/s for $800, which is only a 2.5x factor of improvement.”
Source:
Indeed, though it is difficult to know exactly what proportion of is performed by ASICs, most sources estimate that it is probably .
The “ASIC problem” is largely a non-issue for . This is because an ASIC must have long-term potential to be worth the high upfront cost to miners. Unlike GPUs, ASICs are highly specialized machines specific to the algorithm they are developed for, and are useless for other chains.
With the switch to PoS planned for in the near future, it doesn’t make economic sense for most miners to further massively invest in ASICs for their brief lifespan.
GPU mining != decentralization
The reasoning behind the argument that GPU is more secure is that, in theory. it makes accessible to the layman, and thus more decentralized and resistant to 51% attacks. Regular “at-home” miners can’t afford expensive ASICs, and thus if we want to encourage decentralization, GPUs are a better option.
But in reality, even GPU is largely concentrated in pools or farms, not in the hands of individual hobbyists. Centralization in pools does not happen because ASICs are inaccessible to the layman. Rather, it is because of the benefit that economies of scale provide in giving miners belonging to pools a steadier payout.
Centralization in farms is largely due to the cheap energy available in certain regions.
Source:
GPU friendly is not going to encourage significantly more at-home miners and it won’t dissolve existing pools either. Rather than naively holding onto the hope of making slightly more accessible to a few at-home miners who barely make a drop in the ocean, we should disincentivize those pools which dominate from attacking the system.
Here is where ASICs come in.
Seeing ASICs in a different light
The assumption that ASICs make a network less secure is misplaced. It comes from a failure to consider all the incentives at play. Namely, the fact that the specificity of ASICs is actually a key security component.
An ASIC is a machine whose circuits are designed specifically to run a single hashing algorithm, and are useless for any other purpose, unlike GPUs which are multipurpose and can be used to mine on many different chains. The sunk cost of both ASIC development and investment functions as a one-time entry ticket into network participation.
Such a security expenditure incentivizes ASIC miners to protect the chain in order to preserve the future return on their hefty hardware investment. Whereas a GPU miner does not need to be loyal to any particular hashing algorithm and can simply switch back and forth between chains to optimize their profits, or even repurpose their hardware for non- activities.
Used GPUs can be resold for over 50 percent of their original value, while ASICs resell for only 5 percent of their original value, and that price is also dependent upon the value of the it is specific to.
A key factor in a chain’s security against a 51% attack is whether there is excess hardware available for an attacker to accumulate hash power with. The excess hardware in ASIC mined chains is usually close to zero, but readily available for GPU mined chains.
It’s extremely difficult to quickly acquire enough ASICs to launch an attack even when it is worthwhile to, whereas there are plenty of secondary markets for GPU hashrate and AWS GPU instances. The more general purpose the hardware is, the more available excess capacity there is, and the less secure the chain is against attacks.
This is not merely theoretical — multiple known 51% attacks on GPU coins have already happened. Most recently, Vertcoin and Classic. David Vorick goes into the topic of ASICs as a security feature and Dovey Wan has a thread on why 51% attacks are an evolutionary feature, not a bug, .
Centralization on the manufacturing level
Centralization on the hardware manufacturing level is also a concern for networks, and GPUs are much more centralized on the manufacturing level than ASICs. GPU manufacturing has been largely dominated by three vendors in the past two decades, whereas ASICs remain a highly competitive industry due to the arms race of higher margin.
In the past, while a given ASIC manufacturer may have become the dominant manufacturer of machines for a given hashing algorithm, they have never been able to dominate manufacturing for all chains. It’s possible to overthrow an ASIC leader in a few years, but almost impossible to overthrow Nvidia, AMD, and Intel.
Any update to an established algorithm comes with unproven security risks and the hassles associated with upgrading a worldwide system of miners. The upside of adopting ProgPoW is minimal, since ASICs do not pose a large problem to the network.
And while it is no longer much of a debate for , which is soon to switch to Proof of Stake, other Proof of Work coins still face the question of whether to freely allow ASICs. Those chains should consider whether GPU really does increase the security of their system or if it is, in fact, a security vulnerability in itself.
***
Many thanks to , , , , , and for helping develop these ideas. This article is for research purposes only and we at Primitive Ventures do not currently hold any $ETH, $ETC, or stock in any ASIC or GPU manufacturing companies.
image via Shutterstock
Published at Mon, 11 Mar 2019 09:08:06 +0000


![[bitcoin] #55 bitasean สอนขุดด้วยการ์ดจอ gpu-mining [สายขุดมาทางนี้] [bitcoin] #55 bitasean สอนขุดด้วยการ์ดจอ gpu-mining [สายขุดมาทางนี้]](https://ohiobitcoin.com/wp-content/uploads/2018/05/EEZOxl.jpg)